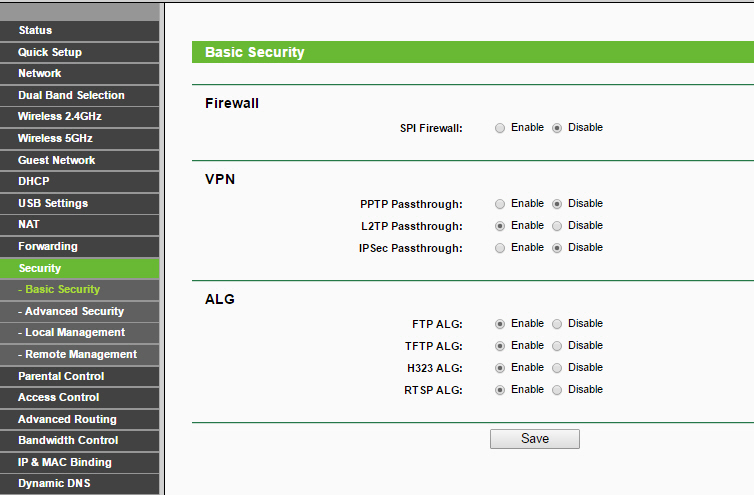
Tech QOTD – It’s outdated, just like some IT budgets… (Topic: Wireless Security)
Tech question of the day (Security+): Examine the figure. What four potential security issues can you identify in the configuration?
(see answer below and video...
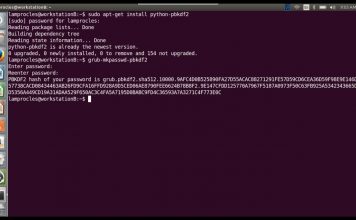
Tech QOTD: Mind your insecurities. (Security+)
Tech question of the day (Security+): Examine the figure. What two insecure configurations can you identify? (Disregard any ALG implications...)
(see answer below and video...
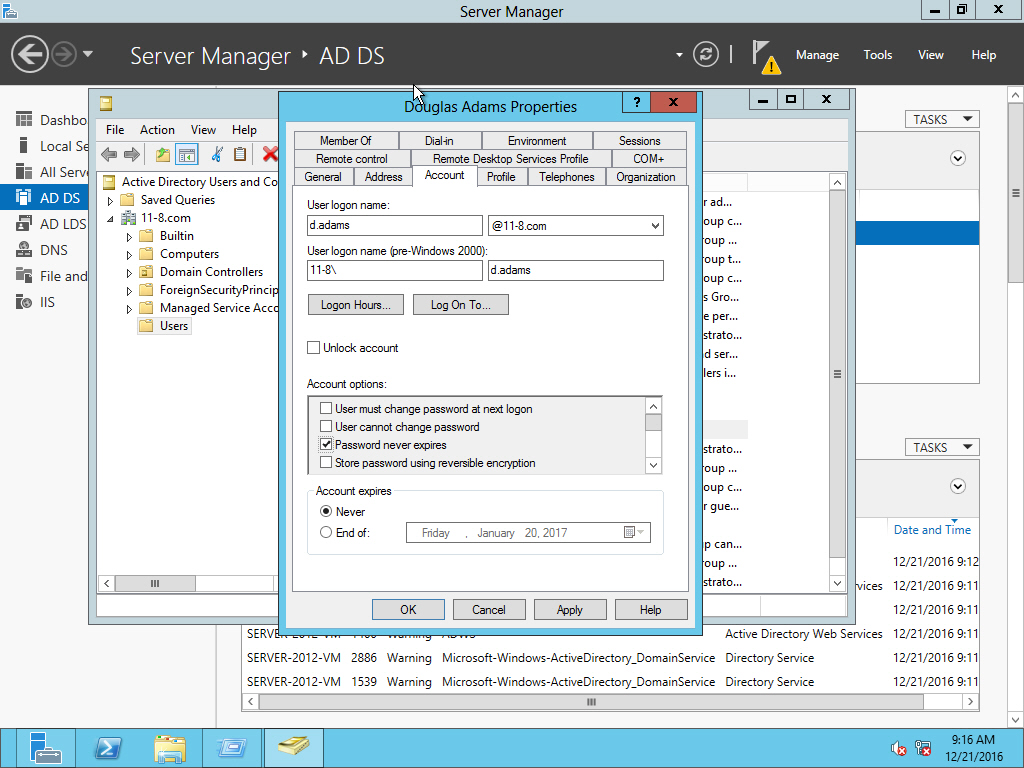
Security+ QOTD: DON’T PANIC, but this user should be cutoff at some point…
Security+ Question of the day: A consultant (Douglas) will be working at your company for three months. Your company has a policy stating that...
Security+ QOTD: This request begins privately…
Security+ Question of the day: What are we attempting to accomplish using the syntax that was typed in the figure? (see answer below and...
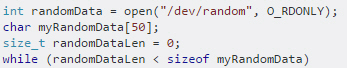
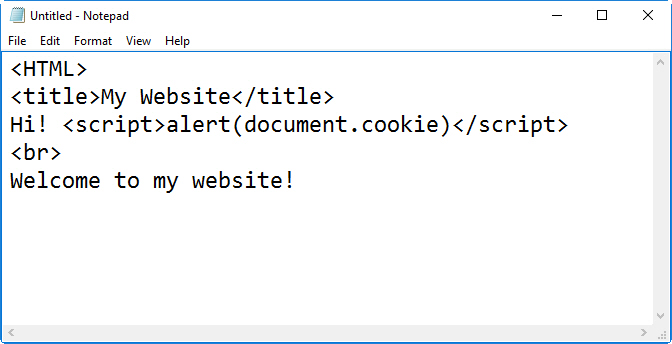
Security+ QOTD: Don’t eat stale cookies…
Security+ Question of the day: What are we seeing in the code shown in the figure? (see answer below and video response.)
//
Answer
We are...
Security+ QOTD: Are you sure of your directory access protection?
Security+ Question of the day: What port number does LDAPS use? (Bonus: What protocol(s) is used to secure it?) (see answer below and...
Security+ QOTD: preservation is our first priority…
Security+ Question of the day: When dealing with OOV, which should be preserved first, RAM or the hard drive? (see answer below and...
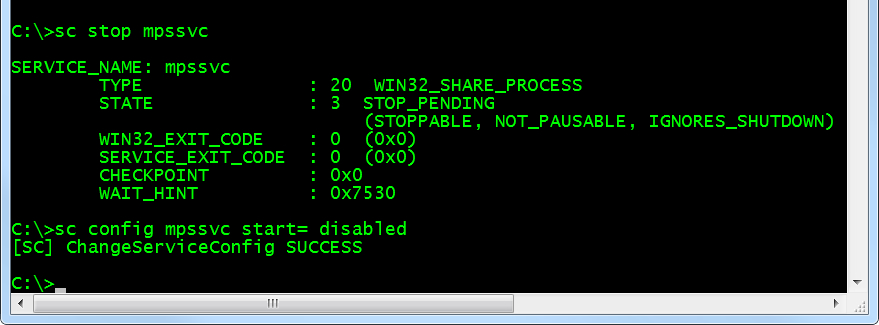
Security+ QOTD: It’s a serviceable issue…
Security+ Question of the day: What is the conventional name for the service that has been stopped and disabled in the figure? (see answer below...
Additional Resources for Learning about Cryptography
- Discusses good sources (websites and books) for information about cryptography (links follow).
Links:
Website: http://www.sy0-401.com
- Discusses good sources (websites and books) for information about...
Recommended Pen Testing Tools
- Describes some of the commonly used penetration testing tools such as NMAP, Metasploit, the Pwn Plug, and Wireshark.
Links:
- Pwn Plug R3
https://www.pwnieexpress.com/product/pwn-plug-r3penetration-testing-device/
- Linksys...