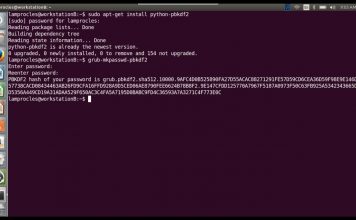
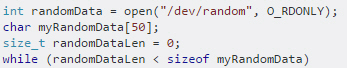
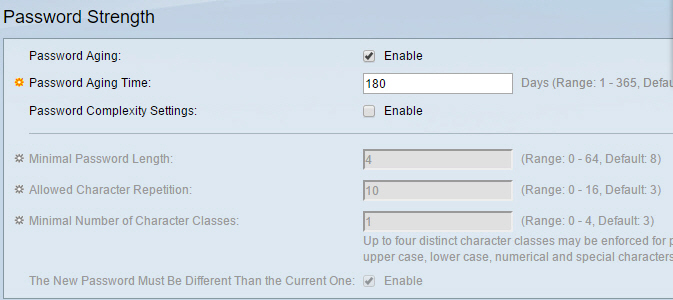
Tech QOTD – Password Security (Security+)
Take a look at the figure. Here we have an Cisco SG200 Switch What are the security issues that you can see? (Click the...
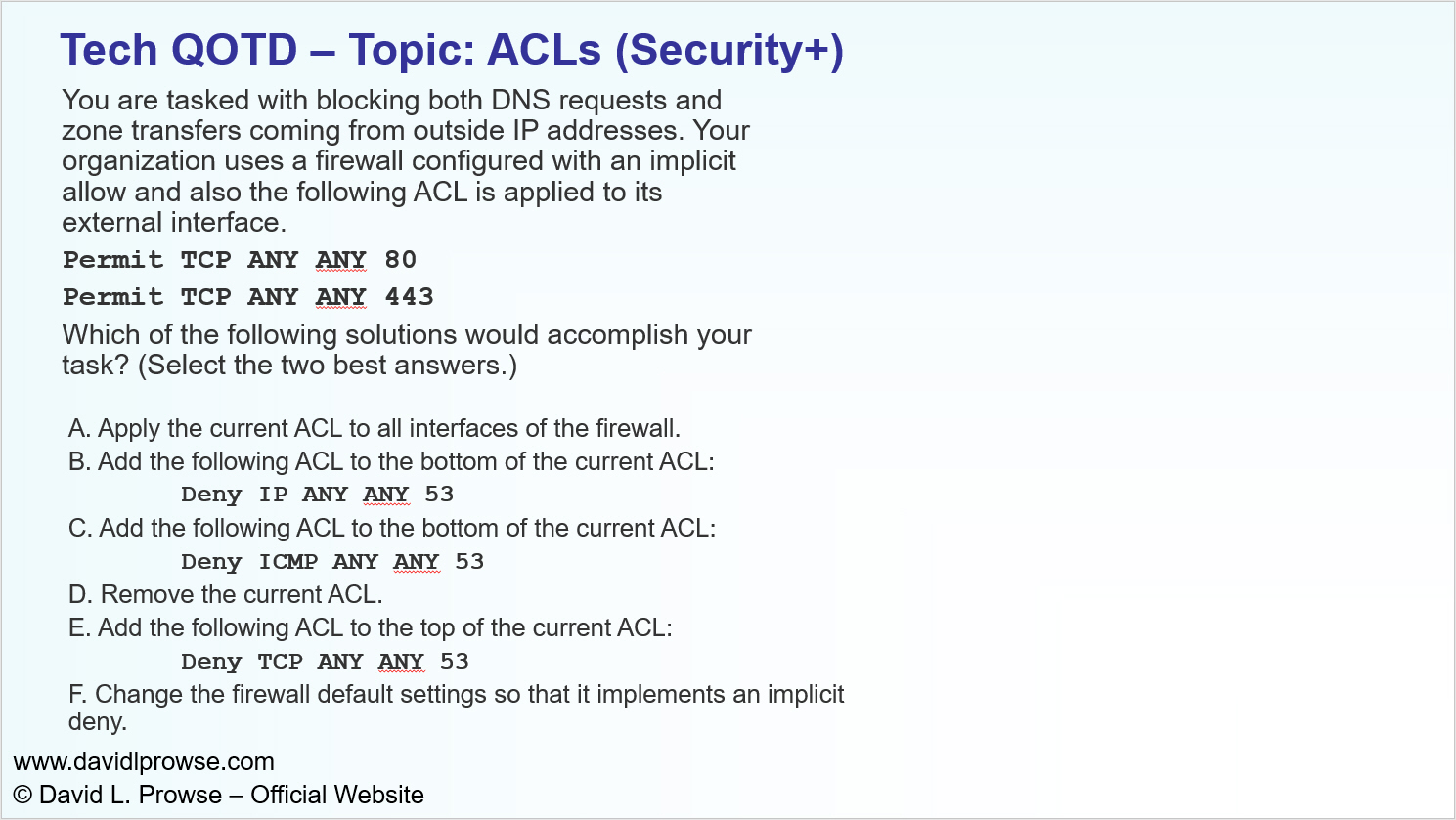
Tech QOTD – Topic: ACLs (Security+)
Answer the multiple choice question below. (Click the image to enlarge.)
(see answer below and video response)
This is just one of hundreds of questions and...
Tech QOTD – Topic: All-in-one Device Security (Security+)
Answer the multiple choice question below. (Click the image to enlarge.) (Text version below.)
(see answer below and video response)
This is just one of hundreds...
Tech QOTD – Security Appliances (Security+)
Answer the multiple choice question below. (Click the image to enlarge.)
(see answer below and video response)
This is just one of hundreds of questions and...
Tech QOTD – Topic: Proximity Security (Security+)
You have decided to install technology that will allow you to identify who enters and exits your datacenter. You are using tags like the...
Tech QOTD – Topic: Application Updates (Security+)
Answer the multiple choice question below. (Click the image to enlarge.)
(see answer below and video response)
This is just one of hundreds of questions and...
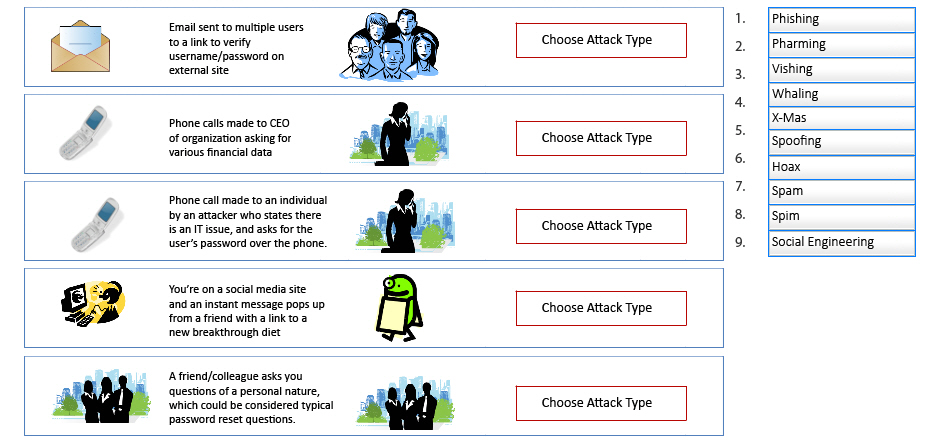
Tech QOTD – Topic: Identifying Social Engineering Attacks (Security+)
Do you know your attacks? Match the type of attack on the right to the appropriate description. (One attack per description.)
This is just one...
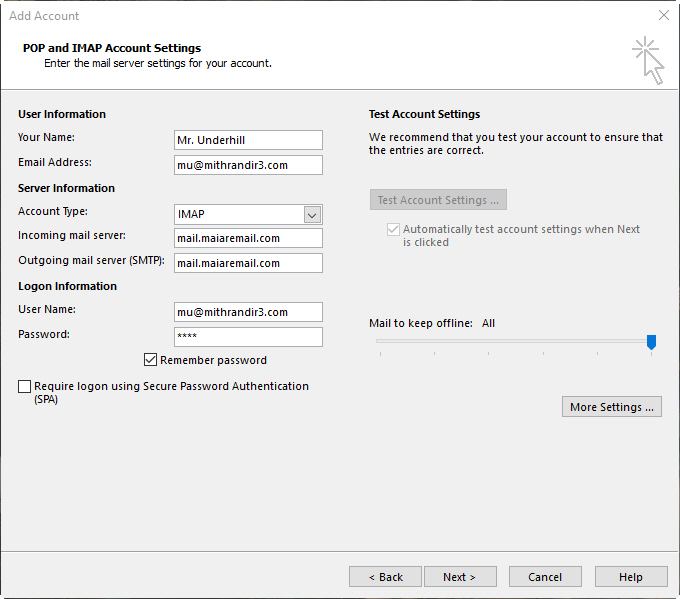
Tech QOTD – Topic: E-mail Connectivity and Security
A user (Mr. Underhill) requires a secure e-mail connection using port 995 for incoming mail and port 465 for outgoing mail. Currently, the user...
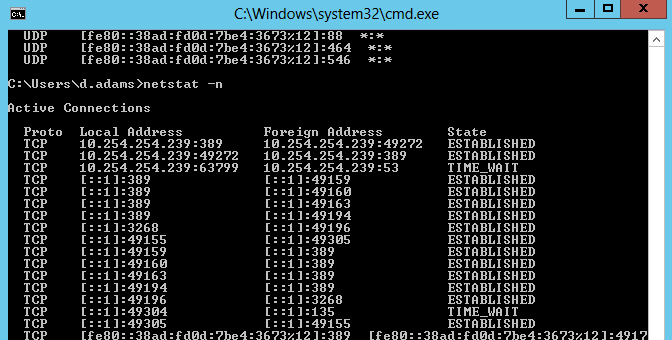
Tech QOTD – Topic: Sign-on Security (Security+)
Tech question of the day (Security+): Examine the netstat results in the figure. What protocol is this computer running for sign-on security? Bonus: What...
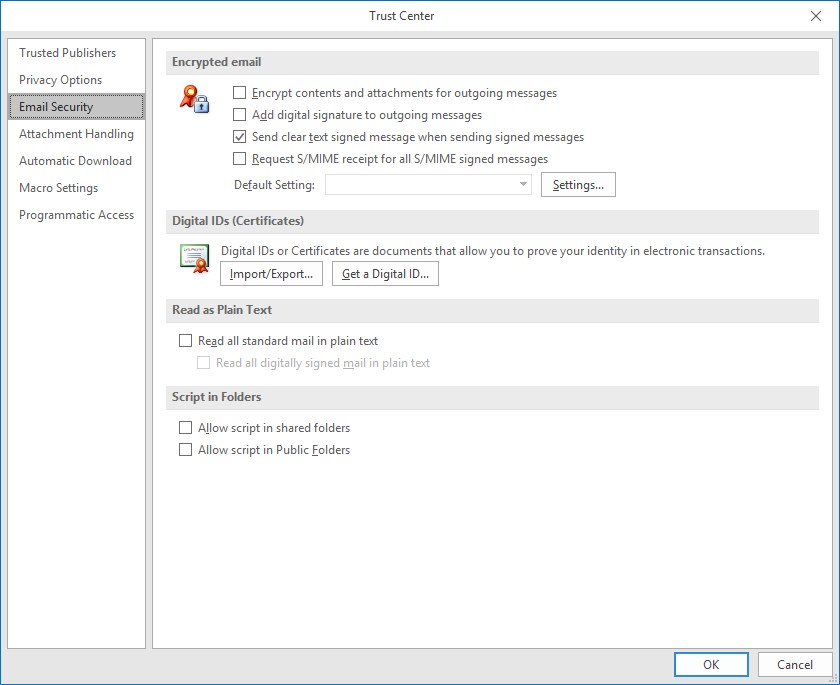
Tech QOTD – Topic: E-mail Security
Tech question of the day (Security+): Your organization is concerned about spear phishing. The CEO wants to improve the overall security posture by proving...